Traceroute to Curtin University:
Blinklist v HTML:
BLINKLIST: - is a specialized web based application for creating a personalized bookmarking site. It has intuitive features designed to file and manage bookmarks according to personal preference and other variables such as favorites, popularity, recently visited and a most used “cloud” which graphically enhances the font, type and color of each bookmarked site in the “cloud” to give a visual overview of the sites that have been visited the most.
The bookmark “tag” that the user attaches to a site enables the link to be filed with other links with the same tag. The intuitive bit happens when Blinklist starts suggesting “tags” based on those you have already used. This provides some consistency in the filing method and should make it easier to maintain lists of references that are managed with an element of personal preference. Multiple “tags” means that the reference link has the potential to relate to any number of related topic enquiries.
Blinklist automates the task of creating and managing a personalized reference library that will become more advantageous as the list expands. This is an end-user application that can be integrated with other applications such as blogs and other Web 2.0 applications.
At first glance, the Blinklist has all the preferred format features such as scannability, easy to navigate and a simple and ordered appearance that make it easy to read and experiment with.
HTML: - reference list has, up to a point, provided the same results as Blinklist and any time difference taken in the initial construction of both lists was probably negligible. However, the html source code would have been very labour intensive and the process would require manual updating each time a new link/reference was added.
The absence of a cross reference link or tag would mean the individual references were isolated from each other and links to other related sites would require separate browser software. This highlights the dependency of this html list version on a server rather than the web (as in Blinklist).
The appearance of the html document is functional and ordered in headings but not graphically enhanced as Blinklist.
My Preference: - would be Blinklist as it is a tailored application that contains a package of features that focus on executing its function. It combines automation to handle large amounts of data and establish relationships within the data, with an ability for the user to include personal preferences e.g. tag names. There are several ways that the data can be stored and accessed and the tags give it access to other related data.
Html is a functional format but would be cumbersome if used to manage large amounts of data manually. It requires other server functions to perform similar tasks that are all contained in Blinklist.
If the web is going to be filled with these types of “Web 2.0” products then using “mashable” applications like Blinklist to expand the potential of other applications like Blogs would be preferable.
A “BLOG” is short for Web-Log or Bulletin-Log. The Wikipedia gives it a pretty good description as a personal website with links. Blogs are published with an expectation or at least a hope it will be read and while the structure allows exclusive access to the author, the links give it the power to be disseminated throughout the Web.
This course is the first opportunity I have had to use a Blog and I’m still coming to terms with its potential. I have seen a variety of Blogs with varying quality and impact on the Web. Some have terrific writing quality but no graphics or links and others appear to be a demonstration of the authors’ artistic ability using graphics in every format possible. I cannot be too definitive about the formats used because I don’t claim to understand them all. However, a program called “Flickr” is being used extensively for photo management and probably “Java” as well.
Having the tools and motivation to publish a personal Website is a powerful thing if there is a story to tell and everyone has a story they want to tell and a Blog lets it happen. Creating and using my Blog has been exciting from the first day I published. With this in mind I was encouraged to “form relationships” on my Blog that would connect me with the community that had similar ideas using links and “key words” in the content.
The content has been devoted to the tasks of school and therefore my main interest is completing the tasks and maybe interacting with the other students who have posted their own Blogs. However, the reason I have chosen the name “Age-Smarter” is to remind me that one of the reasons I have taken this course is to find out if there are any features that the internet can offer to help the elderly (i.e. 75+) or whether there are some enhancements that will help create or maintain their social interaction in an environment where face to face communication isn’t necessary and removes physical barriers imposed by immobility.
Many of the Blogs I have seen have been personal diaries or travel logs, technical information, commentaries on social and Web development issues. Even businesses have published Blogs offering a critique of my Blog and how to improve it. I might visit that site again later.
I have checked out a site that has compiled the best 100 Blogs in
The real value of a Blog is the access to a global population without the immediate need for technical know-how on creating and posting a Webpage using html or Webpage editors. It’s the reverse of Webpage creation in that the content can be posted on a very simple Blog and the enhancements and links can be added later.
Copyright and Trademarks: - http://www.google.com/blogger_dmca.html
The concept of a site for personal and original content should be an important factor when publishing on a Blog. There are many opportunities to use images, and work that should be attributed and or not posted without permission. An author who creates a Blog, while hoping it will be a shared experience should expect some acknowledgement that they own the content and it would not be copied indiscriminately by others.
Censorship: - http://www.blogger.com/content.g
Types of censorship include, obscene and/or types of pornographic language or images. These are perhaps the obvious types of content that censorship used to address. However, in most cases the “content policy” of “blogger” can only place safeguards such as an interstitial (http://en.wikipedia.org/wiki/Interstitial_webpage ), which is a page between the offending pages, warning of the contents so it doesn’t take the reader unaware.
Other types of censorship that are addressed by blogger cover a multitude of other items such as religion, age, gender, disability etc. The level of tolerance accepted by blogger is decided by the law and a threat to report any “illegal” material. Some countries will impose political censorship which block content with key words.
Spam and viruses are not permitted, obviously.
Entering a global electronic environment will mean interaction with people of different countries, religion, morals and standards of communication. Perhaps to make the Blog work in this environment the system has to rely on the “Blog Community” to be socially responsible and impose self censorship.
Evolution:
“Myspace” is a communication room between users; it can create a Blog and has email and chat-room facilities. It has been promoted as a “place” to locate friends and relatives who have lost touch.
“Facebook” is a variation on blogs that enables social interaction within and across networks. My wife uses facebook to post photos and talk to friends within her network which includes people in the local geographical region and overseas.
Each development of a blog demonstrates a significant feature/ utility that differentiates it from other formats. Myspace appears to be an integration of several communication features included in a blog and Facebook is a communication site that allows the uploading of an unlimited number of photos. The user friendly techniques to operate these programs is a key feature of their popularity and can get the user “up and running” in a matter of minutes. Enhancements can then be added once the user is comfortable with the program.
These methods of communication have become an accepted way to communicate using the internet and I can only presume that this generation will continue to adopt future software as it is developed. Therefore, examining how features can meet all generations from young to old will eventually be an expectation of this generation in the near future rather than an optional extra now.
The Web has made huge amounts of information available to society and has been a technological leap in communication and data storage, retrieval and display. Even so, storage and retrieval of data has depended on the ability of search software to find data stored in structured formats (schema) that allow it to be recognized as legitimate data and contain a complete set of attributes before it can be retrieved.
The relational data base relies on the primary key to link related data from different tables and it will not retrieve and display that data if the primary key is missing or different. The Semantic Web, however, has the potential to retrieve data from unrelated databases which therefore requires a more flexible alternative to the traditional notion of the primary key.
SPARQL is a Web 2 software which is an extension of the Web search software that can operate with the existing Web data storage structure whilst accessing the Semantic Web data. In the example of a database, the Semantic Web has access to information which reaches across the data defined in a table.
The ability of this type of software to form relationships with data outside of one database table with data in another database will create “one huge database” and make the next evolutionary leap in data storage and retrieval.
Preference:
The annotation which I have written is a summary of this particular article and provides a description which would give me a more informed and preferable version of the article.
Newman, Andrew, “A Relational View of the Semantic Web”.
Type of Content:
The website I have chosen is a site that contains an article located at O’ReillyXML.com. This is a media website that publishes articles and resource material. The information is more reliable than a site such as a blog but not as proven as a research paper. This site however, reproduces topical articles from many newspapers and magazines.
Search Engine: Yahoo “Semantic Web”
The description of this article, although brief, has more credence because of the website that it appears in i.e. “
The headline of this article is: “A Relational View of the Semantic Web”.
The “blurb” reads “Creating a Web of machine readable information, leading the Web to its fullest potential…” But this is an introduction for a list of articles about the Semantic Web and not directly attributable to this article.
URL: http://www.xml.com/pub/a/2007/03/14/a-relational-view-of-the-semantic-web.html
Author: Andrew Newman 14th March 2007
Institution: O’ReillyXML.com
Summary: “A Relational View of the Semantic Web:”
Abstract:
Software which falls into the category of “Web 2” have the ability to search and find information drawn from databases using applications that are designed to search all data, locate and identify combinations in which bits of data appear and interpret the relevance of the data for the user. This new software has a flexibility that does not need to conform to rigid database design features to conduct a search. The outcome is the integration of data in any database being available and accessible to the user. Therefore, creating the most suitable software to operate within the semantic web and produce these results is the goal of numerous software developers.
Relevance to Purpose:
I selected this article for its relevance to the concept of Meta Data being the data required to produce quality search results in research. The concept of the Semantic Web is an evolutionary step to using Meta Data and the title implies that the relational aspect between types of Meta Data is an important factor it the development of the Semantic Web.
Purpose of the Site:
This site would be described as commercial because it invites subscription to its service for a fee and has an abundance of advertising material on it. It sells books on line and reference material can be downloaded for a fee. However, the article is valid and the information can be tracked to a reliable source.
O’RiellyXML.com is a resource and publishing center. To post to the site membership is required but articles are free to read. It would be a useful search tool for future reference.
The Journalists who wrote this article are recorded in the search results. The facts noted in their article are suitably referenced in the Bibliography for authenticity. The credentials of the author are available on a separate reference page:
Andrew Newman
“Andrew Newman is currently working for the
The article is published by “© 2008, O'Reilly Media, Inc.”. The Website produces a directory of articles about the topic but states at the foot of the page that copyright is owned by the individual authors. There is an invitation on the site to submit articles on topics that are new and “it helps if you know that we tend to publish "high end" books rather than books for dummies, and generally don't want yet another book on a topic that's already well covered.”
The content of articles is talking about a new area of Web use in the Semantic Web. The article doesn’t lend itself to being bias unless support for the Semantic Web concept is bias. There is a substantial amount of information and speculation that is supported by explanatory data and a bibliography.
Other articles about the topic are published on the same site and are listed in the directory. Also using Google I found 27 related sites:
Currency:
The date of the article was recorded on the search results. The development of this concept will make each article time sensitive because of the changing technology. However, this site seems to be a popular resource for publications and attracts current information on the topic. A search of this site on the Semantic Web produced 9,842 references to similar articles. The range of posting dates appears to be from 2000 to 2008 but they are not listed in date order and required a manual search for the information.
Signs of Recognition:
Links to http://www.xml.com/semweb/ (above) – 6 (3 are blogs, 2 are linked to the publisher’s Webpage and 1 is an educational reference.
Tags for this Site:

Tags for www.xml.com (above) – 13 bookmarked items from this site used by 5,585 people. Is this a significant number of tags for this type of site? A search in del.icio.us for “Semantic Web” resulted in 23,915 bookmarked items by thousands of people. This doesn’t place www.xml.com as a popular website for this information.
Blog reaction to website www.xml.com 1,432 The “authority rating” is respectable for the blogs on a specialized topic. A search for blogs with references to the “semantic web” was 8,281. Not all references from xml.com are about the semantic web so more comparison would have to be made to determine whether bloggers thought this site is popular.

Blog reaction to website www.xml.com 1,432 The “authority rating” is similar for these blogs as the previous but would need some more comparison with other sites to get the relative popularity.
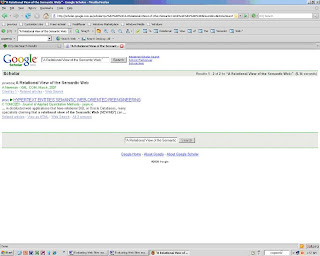
Citations of Articles by other Researchers: This is a search using the title of the article to see whether it has been cited in any research articles. The search found that the article had been cited in one published paper.
Boolean searching task:
The biggest number of hits relating to these key words:
Using OR:
Semantic OR Web: would initiate a search for the individual words or both words combined.
Semantic
http://www.google.com.au/search?hl=en&as_qdr=all&q=semantic&btnG=Search&meta
Web
http://www.google.com.au/search?hl=en&as_qdr=all&q=web&btnG=Search&meta
Semantic OR Web
| Search Items | Results |
| Semantic | 23,600,000 |
| Web | 4,210,000,000 |
| Semantic OR Web | 4,230,000,000 |
Information most relevant to what I actually wanted to look for:
Using Semantic AND Web AND Concepts: would initiate a search of sites that only contained these words and as I was searching for information on the concept of the Semantic Web, I could exclude reference to “applications”by using NOT and ().
(Semantic AND Web AND Concepts) NOT applications: http://www.google.com.au/search?hl=en&as_q=&as_epq=Semantic+Web+concepts&as_oq=&as_eq=applications&num=10&lr=&as_filetype=&ft=i&as_sitesearch=&as_qdr=all&as_rights=&as_occt=title&cr=&as_nlo=&as_nhi=&safe=images
Using Google, the number of results using a Boolean search with these parameters, came to 49.
Google doesn’t seem to recognize the Boolean Operators and substitutes its own “Implied Boolean Logic” instead with the use of + & - symbols. The following site address provides a list of corresponding Boolean Operators used by Google: http://www.googleguide.com/advanced_operators_reference.html
Information coming only from Universities:
Searches using different search engines would reveal different search results and each search would require several modifications to narrow down the search to get the best quality information.
URL: http://www.xml.com/pub/a/2007/03/14/a-relational-view-of-the-semantic-web.html
Author: Andrew Newman 14th March 2007
Institution: O’ReillyXML.com
Summary: “A Relational View of the Semantic Web:”
Software which falls into the category of “Web 2” have the ability to search and find information drawn from databases using applications that are designed to search all data, locate and identify combinations in which bits of data appear and interpret the relevance of the data for the user. This new software has a flexibility that does not need to conform to rigid database design features to conduct a search. The outcome is the integration of data in any database being available and accessible to the user. Therefore, creating the most suitable software to operate within the semantic web and produce these results is the goal of numerous software developers.
Search Engine: Yahoo
URL: http://www.sciam.com/article.cfm?id=the-semantic-web
Author: Tim Berners-Lee, James Hendler and Ora Lassila
Institution: Scientific American magazine May, 2001
Summary: “The Semantic Web:”
“The Semantic Web is not a separate Web but an extension of the current one, in which information is given well-defined meaning, better enabling computers and people to work in cooperation. The first steps in weaving the Semantic Web into the structure of the existing Web are already under way. In the near future, these developments will usher in significant new functionality as machines become much better able to process and "understand" the data that they merely display at present.”
Search Engine: Copernic Agent
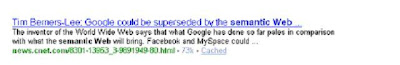
URL: http://news.cnet.com/8301-13953_3-9891949-80.html
Author: Posted by Dan Farber
Institution: cnetnews.com
Summary: “Tim Berners-Lee: Google could be superseded by the semantic Web:”